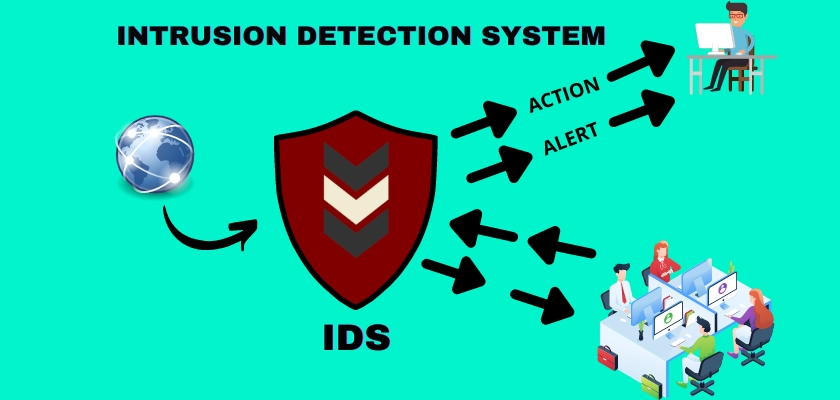
Intrusion detection system is a key factor in the world of networking. Networks have been in existence for a very long time and have played a vital role in bringing the world and people closer to each other. But along with the benefits of networks is also the threat or threats to networks.
IT departments of enterprises deploy intrusion detection systems to identify potentially malicious activities within their organizations. This method of ensuring security has been well documented and explained in this piece so as to enlighten and guide you.
What is an Intrusion Detection System?
An intrusion detection system, Also known as IDS, is a system that is used to monitor the traffic of a network for any suspicious activity and take actions based on defined rules.
An intrusion detection system can scan a system or a network for policy breaching and harmful activities. Any violation, or malicious activity will be reported to the administrator normally or it will be collected using an effective SIEM system, also known as security information and event management.
A brief explanation of a SIEM is below;
A SIEM integrates outputs from various sources and then utilizes different alarm filtering techniques to differentiate malicious or suspicious activity from wrong alarms.
Even though an intrusion detection system monitors networks for potentially malicious activity commonly, the system is also disposed to false alarms. That is why organizations have to fine-tune their intrusion detection systems when installing them. This means they need to focus on setting up their IDS properly to enable them understand what normal traffic on their network is.
Ultimately, identifying a malicious activity will become easier for the system in the best possible way.
See the best Intrusion Detection and Prevention Systems (IDS IPS) for 2022
How does an Intrusion Detection System work?
Attackers commonly use multiple approaches when they attempt to penetrate any system. However, with an effective network intrusion detection system in place, knowing the kind of attacks or intruders is very important. This is because this approach will help you prevent any security threats in the best possible way.
An intrusion detection system functions by monitoring both inbound and outbound traffic over a network. It analyzes activities continuously for changes in traffic patterns. In case of any malicious or suspicious activity, the system alerts the systems administrator immediately.
The administrator can then review alarms and take appropriate actions to mitigate any threat in the best possible way. Furthermore, to ensure that an intrusion detection system is not going to slow down the overall network’s performance, these systems are commonly based on the switched port analyzer.
It is worthy of note that an intrusion detection system may only inform of suspicious activity while an intrusion detection and prevention system will inform and act against any suspicious activity.
Regardless of the type of intrusion detection system program you have, it can help you to:
- Identify malicious attack patterns within your network packets.
- Determine any abnormal activity in network traffic.
- Monitor the behavior of users.
- Ensure that the activity of the system and user isn’t going against the network guidelines.
All of these things will ultimately help improve the security and performance of your network in the best possible way.
Types of Intrusion Detection System
Do you want to know about some of the most important types of intrusion detection systems? Let’s get to know about these below to know more.
So, here we go:
(1) Host Intrusion Detection System
Also known as HIDS, these systems are commonly run on independent devices or hosts on the network. A Host Intrusion Detection System will monitor both outgoing and incoming packets from your devices only. It will also alert the network administrator if any malicious activity is noticed.
HIDS takes a snapshot of current files of a system and compares them with previous system files. For example, the system will send an alert to the administrator of the network for file changes such as deletion or editing.
For example, HIDS can be used to monitor critical machines that are not meant to change their layout.
(2) Network Intrusion Detection System
Also known as NIDS, these intrusion detection systems are set up at particular points planned within a network to monitor and examine network traffic from all the devices connected to the network. This system will perform an observation of passing traffic on overall matches and subnets to a collection of known security attacks or threats.
Once the system has identified or observed an attack or any abnormal behavior, it will send an alarm to the network administrator to take further actions. The administrator will then immediately try to discard the malicious activity happening over the network to ensure security in the best possible way.
For example, you can install a NIDS on the subnet where your system firewalls are located. It will then help you identify if someone is trying to crack your firewalls.
(3) Intrusion Detection System Based on Application Protocol
APIDS is an agent or system that resides within a servers’ group. It will identify an intrusion by interpreting and monitoring the communication on the protocols specific to the application.
(4) Intrusion Detection System Based on Protocol
PIDS is the IDS based on protocols. These systems are based on the agent or system that continuously resides at the server’s front end. It also controls and interprets the protocol between a device or user and the server. It provides security to a web server by regularly monitoring the HTTPS stream.
(5) The hybrid Intrusion Detection System
Hybrid IDS are commonly made by using two or more approaches of an IDS. In this type of intrusion detection system, data or host management is usually combined with the information of the network to create a full view of a network system.
Most importantly, hybrid IDS is a more effective solution when compared with other types of intrusion detection systems.
Key benefits of an IDS
Do you want to know how an intrusion detection system can benefit an organization or enterprise? An intrusion detection system is mainly programmed to work as an effective security solution for any deployment. Other than that, an IDS can benefit you in various other ways. Let’s get to know about these benefits below to understand things better in this regard.
So, here we go:
Fewer security threats
Even though the connected units to any network are commonly unable to notice any changes in the traffic’s behavior, an intrusion detection system will make sure to cause less disruption to an organization’s systems. It will also ensure to reduce the number of security-related incidents in the best possible way.
Enhanced privacy protection
The intrusion detection system will compare the traffic of a network against a list of already known malicious traffic. However, to ensure the highest level of privacy protection, the system will not view or read the content available.
Selective logging
Keep in mind the fact that an intrusion detection system usually compares the traffic of your network only against known malicious attacks when it is going to take any action. It won’t log the activities of users to maintain the privacy of users who are using the network.
Reputation managed protection
An intrusion detection system also subscribes to a list of popular malicious sites and domains based on their reputation. The system will use this list to protect your organization proactively in the best possible way.
Dynamic threat response
You can fine-tune your intrusion detection system to recognize and respond to certain security threats more effectively. This will allow the system to react accordingly when identifying those specific threats.
Multiple threat protection
The intrusion detection system also offers quick threat protection. This helps organizations to mitigate brute force attacks. Most importantly, it can offer you enhanced protection against multiple availability threats as well.
Key challenges of an IDS
An intrusion detection system usually has several known challenges that may be more than what an organization is able or willing to take on. Let’s have a look at the common challenges of an intrusion detection system below to know more:
Staffing
Based on the particular requirements of any organization, an enterprise must be ready to make an intrusion detection system that can fit those specific needs. It means that an IDS can never be a fit for all solutions, especially if you want it to work effectively and accurately for your organization.
For this, you need to get help from professional IDS analysts who can customize an IDS product based on the interest and needs of any given site or network. While well-trained and professional IDS analysts are not common, staffing can be a great challenge for organizations that want to make a customized IDS product.
False positives
False positives mean an IDS generates alerts when there is no actual problem in the system or a network. However, you can send the alerts to a secondary analysis platform to fix this problem.
Overall, this IDS challenge can put more pressure on the IT professionals of an enterprise. This is because they need to keep updating the information of their Intrusion detection systems continuously with the right info. With this, detecting legitimate threats and distinguishing those actual threats from the allowable traffic can become easier in the best possible way.
This task isn’t easy as it seems to be, this is so because an IT administrator must tune the IDS products to analyze the appropriate context as well as to decrease false positives.
Even more, there are also some circumstances in which properly valid activities can also generate false alarms just as a matter of probability. However, organizations more commonly prefer to choose another secondary traffic analysis system, just like the SIEM (security incident and event management) platform.
This secondary analysis system usually works with IDS to help in investigating the right alerts in the best possible way.
Missing out on any legitimate risk
The trick with an intrusion detection solution is that it needs to know what the attack is for identifying it. As a result, an IDS product always suffers from the problem of patient zero.
IDS technology always has trouble detecting malicious activities with encrypted traffic, according to experts. Even more, the distributing nature and speed of the incoming traffic on a network can also restrict the effectiveness of an IDS in any enterprise.
How to choose an IDS
Are you trying to choose between a network-based or a host-based intrusion detection system? Before choosing, you should note that the purposes for both of them are different. In the majority of cases, both of these systems work simultaneously. Therefore, companies prefer to choose a tool that can provide both of these solutions at the same time.
However, a host-based intrusion detection system works to detect internal changes, for example, a virus downloaded by an employee accidentally. While on the other hand, a network-based IDS detects malicious packets immediately they enter a network. It also notices any unusual behavior on networks, such as protocol-specific attacks and flooding attacks.
An intrusion detection system deployment requires consultation in the process. These people include information security officers, management, system admins, network admins, database admins, and people who deal with sensitive data security.
This is so because all of them will have a better idea about the vulnerabilities of your network security. For example, the best location for the deployment of the intrusion detection system can be provided by them.
On the other hand, if you aren’t going to involve these crucial people in decision-making regarding IDS. You may miss a lot of network vulnerabilities you need to focus on. So, the best approach is to hold a meeting before deploying and setting up your intrusion detection system.
Final Thoughts
IT departments of enterprises use intrusion detection systems to identify any malicious activities happening in their network environments. The overall purpose of this cyber security staple is to inform the IT team if any network intrusion takes place. Alerting information of the IDS commonly includes intrusion’s source address, the victim address, and the attack type that happened.
All the IDS products are programmed to properly analyze traffic and identify the patterns of traffic to indicate any cyber attack. Most importantly, these systems are designed to identify different types of cyber attacks with ease. So, overall, detecting any traffic that is problematic to software is going to become easier for IT professionals of any organization.
Even more, these systems are also here to reduce cyber security threats in the best possible way. Due to the increasing effectiveness of intrusion detection systems, more and more enterprises are incorporating these as an essential security solution to their overall networks.
Pretty! This has been an extremely wonderful article.
Thanks for supplying these details.