
The Palo Alto 3220 Next Generation Firewall is here, and this review is designed to give you our first-hand experience with this machine. Now, in the ever-evolving landscape of cyber threats, the need for a formidable solution has never been more crucial. As the digital world advances, so does the complexity of threats. The Palo Alto PA-3220, and Palo Alto Firewalls generally can provide you with the sophistication you need, and may be the solution you require for Advance Threat Detection, High Performance, Scalability, and Operational Efficiency.
The Palo Alto 3220 Firewall is designed for High-Speed Internet Gateways, provides granular Application Visibility and Control, Content Inspection, URL Filtering, Antivirus and Anti-Spyware Scanning, et cetera. The Palo Alto 3220 Firewall doesn’t stop at perimeter defense, as expected of a top-tier Next Generation Firewall, it provides robust Intrusion Detection and Prevention to mitigate against known and unknown threats. Above surface-level defenses, the PA-3220 scrutinizes Encrypted Communications, secures all traffic, provides redundancy, dedicated memory and processing for your entire Network, its own Security, Management, and Threat Prevention.
Our review of this Palo Alto PA-3220 Next-Generation Firewall will look at its Architecture, High-Availability Configurations, its ability to integrate with Lightweight Directory Access Protocol (LDAP) and Active Directory, Virtual Private Network functionality, Logging and Reporting, Automation, and how it empowers you as a Network Security Administrator to monitor, generate reports, and proactively analyze security events.
Overview of the Palo Alto 3220 Front Panel

Firstly, looking at the appearance of the Palo Alto PA-3220 Firewall, you immediately observe its visually appealing and distinctive blue color. Factors such as heat dissipation, and material durability are very evident in this machine. From left to right, the Palo Alto 3220 Front Panel has 12 RJ-45 Ethernet Ports. These ports are capable of 10Mbps/100Mbps/1Gbps and their Link Speeds and Link Duplexes are Auto-Negotiate Only. Next, on the Front Panel of the PA-3220 are SFP Ports from 13 to 20. Ports 13 to 16 are capable of 1 Gbps, while Ports 17 to 20 are capable of SFP and SFP+ (10Gbps) according to the installed transceiver. It is worth mentioning that the Palo Alto 3220 Firewall is in the Palo Alto PA-3200 Series of Next Generation Firewalls, and the other Firewalls in this series are the PA-3260 and PA-3250. Still on the Front Panel of the Palo Alto 3220, the next port you have is the HSCI Port. This means High-Speed Chassis Interconnect and used for High Availability Session Setup Traffic.

Next on the Front Panel of the PA-3220 are four Ethernet Ports known as HA1-A, HA1-B, MGT, and Console. The HA1-A and HA1-B are dedicated Ports that enable you to connect two Palo Alto PA 3220 Firewalls together for control and synchronization of traffic. We did test this setup and you can have an Active/Passive setup or an Active/Active setup. In the former, one of the Firewalls is active and the other is on standby, and in the event of a failure of the first, the second kicks in seamlessly. While the Active/Active setup has both Firewalls operational at the same time. Moving on, the MGT Port is the Management Interface where you can simply connect an Ethernet Cable to it and to your PC to access the PA-3220 via its Graphical User Interface. Then, the Console Port obviously enables you to connect to the Firewall using a Terminal Application. Next, you will observe a USB Port on the Front Panel. This allows you to plug in a USB Flash Drive that contains a Bootstrap PAN-OS Bundle Config and with this, you can speed up the process of Configuring and Licensing the Palo Alto 3220 without internet access. Still on the Front Panel, the next port you would find is a Micro USB Port. This gives you the option of using a standard Type-A USB-to-micro USB cable to connect to the PA-3220 and to your PC. Lastly on the Front Panel of the Palo Alto PA-3220 Firewall, you find eight LEDs that show you the state of the Firewall’s hardware. These are; Power LED (Green when the machine is turned ON, and OFF when the machine is not powered). Status LED (Green when the machine is operating normally, and Yellow when the machine is Booting). High Availability LED (Green when the machine is in a dual setup and it is the Active one in an Active/Passive setup, Yellow when the machine is the Passive one, and OFF when High Availability is not configured). Temperature LED (shows Green when the PA-3220’s temperature is normal, and Yellow when the temperature is outside tolerance levels). Alarm LED (Red shows up when there is a hardware failure, and OFF when the machine is operating normally). Fans LED (A Green LED when the fan tray and all fans are fully functional, and Red when any out of the three fans fails). Power 1 and Power 2 LEDs (Power 1 is for the Power Supply that’s on your left-hand side when looking at the back of the PA-3220, and Power 2 is to your right. A Green LED indicates that both Power Supplies are functioning properly, and Red indicates a fault). Ethernet Port LEDs (For RJ-45, the left LED shows Green when there is a network link, the right LED blinks Green when there is network activity). SFP, SFP+, and QSFP LEDs (A solid Green means a network link is established, and a blinking Green means network activity).
Overview of the Palo Alto 3220 Back Panel

On the back panel of the Palo Alto 3220, you find its redundant power supplies, fan tray, and LEDs. For the power supply units, the LED at the top shows you the status of the power input and the lower LED shows you the status of the power supply output. Input LED (Solid Green indicates that the Input Voltage is within the correct specifications, Blinking Green indicates Overvoltage or Undervoltage, OFF means no power or the voltage has exceeded Overvoltage or Undervoltage specifications). Output LED (A Solid Green indicates no power supply warnings or faults, Blinking Green indicates Standby Output is enabled and no faults detected, Blinking Yellow indicates that a power supply warning has been detected, and Solid Yellow indicates that there is a power supply fault). Fan Tray LED (Green indicates that all three fans and the fan trays are fully functional, Red means that a fan or multiple fans have failed).
The Package Components and Accessories

When you unpack the Palo Alto 3220 Firewall, you will find the machine itself, AC Power cords, velcro straps, a DB-9 female to RJ-45 male console cable, a Standard Type-A USB to micro USB Console Cable, a Standard RJ-45 CAT6 Ethernet Cable for Management Port Access, Rack Mount Brackets for a Two-Post mount and if you ordered Four-Post Rack Mounts, you will have that as well. Then you have #8-32 x 5/16 inch Rack-Mount Bracket Screws to attach the front rack-mount brackets to the Palo Alto 3220. Also, #10-32 x 3/4 inch Rack Mount Screws to fix the front rack-mount brackets to a #10-32 hole, as well as #12-24 x 1/2 inch Rack Mount Screws to fix the front rack mount brackets to a #12-24 hole. Lastly on this, you have an End User License Agreement document and RoHS declaration.
How to Set up the Palo Alto PA-3220 Firewall
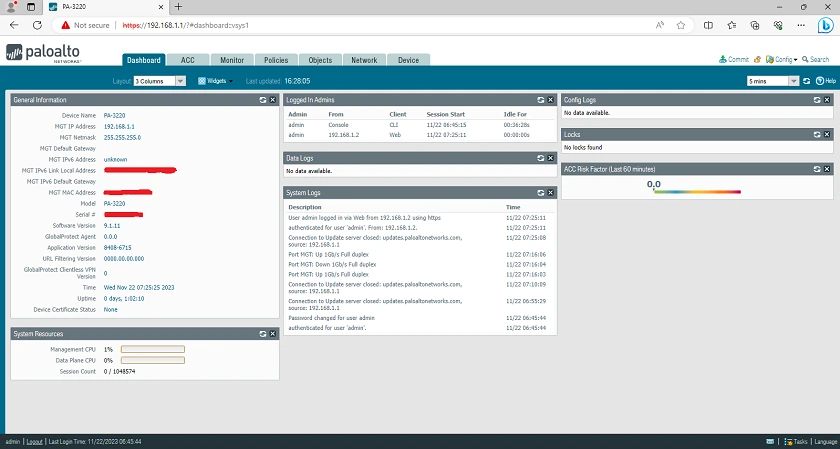
Now, depending on your data center’s rack space availability, you can mount the Palo Alto 3220 on a Two-Post or Four-Post equipment rack. Also, it is advisable to power it up and integrate it with your Local Area Network before proceeding to mount it in your data center, except if you are fine with mounting it, connecting all your network cables, and then accessing the PA-3220 remotely from your desk. With this said, proceed accordingly and if you have the Palo Alto 3220 mounted or it is on your desk, the default IP Address to the machine is 192.168.1.1/24. The Username and Password to the machine are admin and admin respectively. When you log into the Palo Alto 3220 for the first time, you are required to change the Password to something more secure. Then, if you are remotely accessing the machine, you should have changed the default IP Address to another that’s on the same subnet as your LAN and your PA-3220. To make this happen, connect the Cat6 standard RJ-45 Ethernet Cable to your PC’s Ethernet Port, and the other end of the cable to the Management Port on the Palo Alto 3220 Firewall. Now, assign an IP Address to your PC, in the same subnet as 192.168.1.1/24 like 192.168.1.2/24. When this is done, open your Browser and type https://192.168.1.1 and you should see the Dashboard of the PA-3220 show up. If you see ”this page is not secure” when you type the IP Address, simply ignore it and proceed. The picture below shows you what the Dashboard looks like.
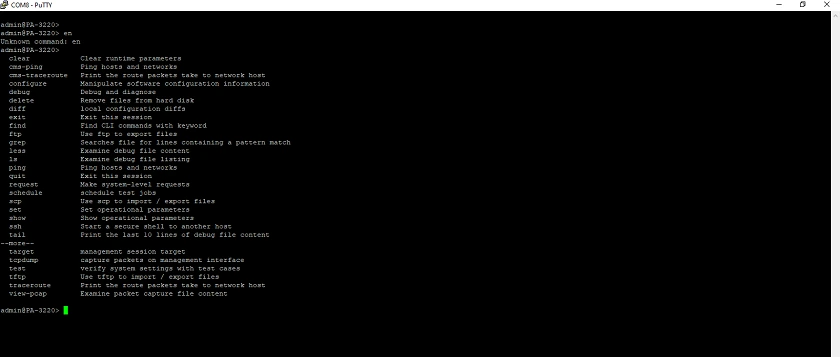
To give you an idea of what the Command Line Interface of the PA-3220 looks like, the picture below shows this.
If you want to have High Availability and a more redundant setup, you can use two Palo Alto 3220 machines where they can be configured to be in an Active/Passive state or an Active/Active state. A redundant setup can also go all the way to sixteen machines. We recommend the Active/Passive setup as it is simpler to configure and deploy. For this, you need to enable High Availablity on both PA-3220 Firewalls, Configure the same Group ID Value on both so as to have a virtual MAC Address, then set High Availability Modes on both Firewalls to Active and Passive respectively, enable Preemption on both Firewalls with Device Priority set to a low value for the Primary Palo Alto 3220. To carry out the physical connections, simply connect an Ethernet Cable from the HA1-A Port on one of the Palo Alto 3220 machines to the HA1-A Port on the other. Then, another Ethernet Cable from the HA1-B Port on the first PA-3220 to the HA1-B Port on the second. The remaining steps will be to configure Encryption on this link, as well as enable Heartbeat Backup.
Palo Alto PA-3220 with LDAP Authentication and Active Directory
These features require you to perform some steps which are; Creating and Adding an LDAP Server Profile, Adding LDAP Servers, Ports, IP Addresses, FQDNs, Server Type, Base DN, Bind DN and Password, set Timeout, Retry Interval, and Enabling SSL/TLS Secured Connection. That’s not all, the next steps are to Assign the Server Profile to Configure an Authentication Profile and Sequence, and also Assign the Authentication Profile to the Firewall Application that requires the Authentication.
Features and Performance of the Palo Alto 3220 Firewall
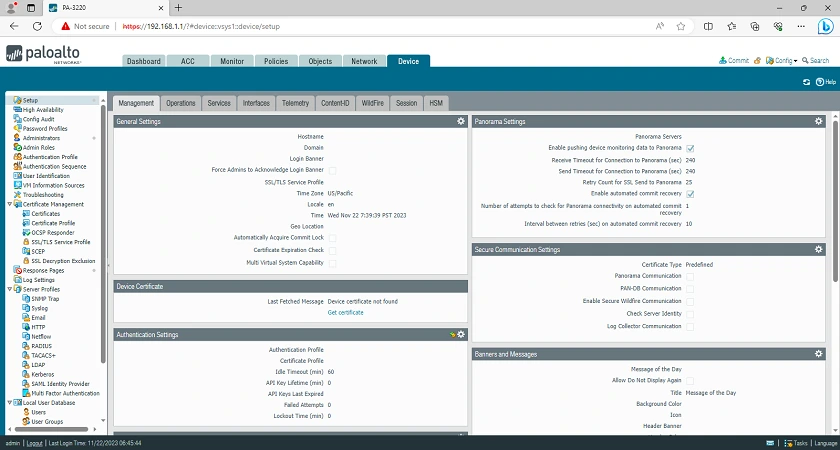
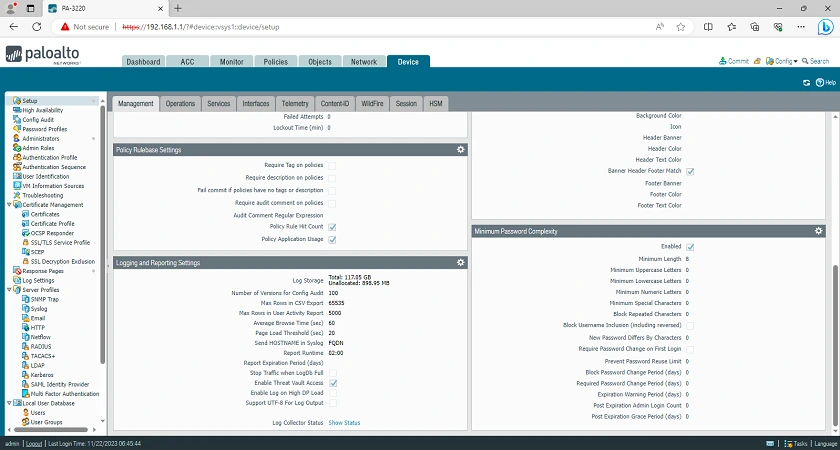
Firstly, with the Palo Alto 3220 Firewall, or even any of the models in the series, you cannot go wrong, except price is at the top of your deciding factors. The Palo Alto 3220 is an extremely powerful, versatile, and advanced security solution that caters to networks of all sizes, offering advanced threat detection and prevention capabilities with detailed network visibility. As seen in the screenshots above, it is built with a vast array of features and settings.
The Dashboard or Graphical User Interface of the Palo Alto 3220 Firewall gives you full managebility of the machine. It is the nerve center for you as an Administrator to Monitor Network Activity, view Real-Time insights into traffic patterns, Manage Application usage, and respond to situations you observe, or receive alert notifications about. The features of the Palo Alto 3220 Firewall are very many but we’ve summarized them in the following points:
(1) Throughput and Performance
At the core of the design of the Palo Alto 3220 Firewall is its classification as a Next Generation Firewall. With this, the machine’s throughput capabilities are top-notch. It is able to handle very large volumes of traffic without sacrificing performance. This makes it very suitable for deployments that demand high bandwidth and the needs of modern enterprise networks.
(2) Behavioural Analytics and Machine Learning
The Palo Alto 3220 Firewall is built with learning algorithms that enable it observe and analyze patterns of behavior in your network. This predictive mechanism enables it to recognize potential security threats, and proactively provide defense against zero-day attacks.
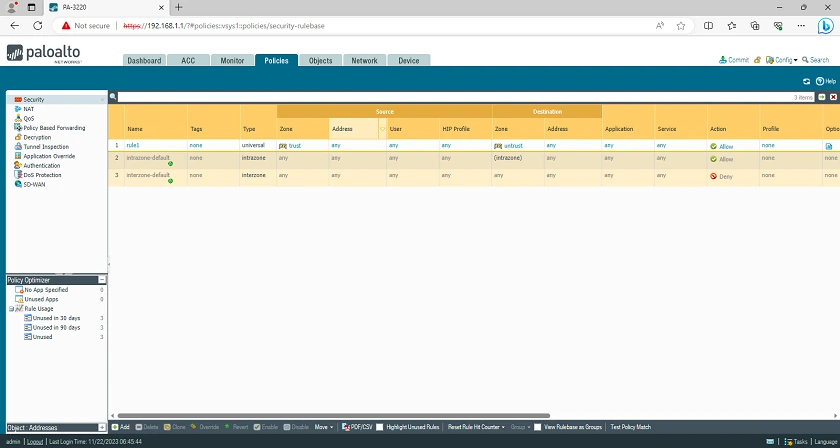
(3) Multi-Zone Segmentation
This feature of the Palo Alto 3220 Firewall enables you as an Administrator to create distinct Security Zones within your network infrastructure. This is extremely beneficial as segmentation helps to isolate different parts of the network infrastructure, and in the event of a security breach, lateral movement is blocked.
(4) URL Filtering and Content Inspection
This is another useful feature of the Palo Alto 3220 Firewall. It provides access control to websites based on policies and categories. URL Filtering fortifies your security by scrutinizing websites and applications. An Organization can set internet usage policies to control and prevent visits to inappropriate websites.
(5) GlobalProtect VPN
As expected of a top-tier Next Generation Firewall, the Palo Alto 3220 provides secure and encrypted remote access. Network Administrators and Organizations as a whole can enable secure remote access for their mobile workforce.
(6) Role-Based Access Control
As a Network Administrator, you can have a Superuser Account on the Palo Alto 3220 machine. You can also designate other users as Superusers or reduce the power of their accounts. This helps to enhance security governance and ensures that only authorized persons have access to specific areas of the Palo Alto 3220’s interface and configurations. You can even set user accounts to have read-only access.
(7) Geolocation Based Policies
The Palo Alto 3220 Firewall gives you more than enough Policies to configure. Location-based policies are available for you to implement according to the geographic origin of network traffic.
(8) Centralized Management using Panorama
Panorama provides a streamlined approach to Policy Enforcement, Monitoring, Reporting, and Consistency. With the Palo Alto 3220 Firewall, you can manage all these using Panorama for a centralized approach and consistency in your network security management.
(9) Custom Application Signatures
In its operations, the Palo Alto 3220 uses a combination of signature-based and signature-less techniques to mitigate and deal with threats. Then, in terms of Custom Applications, you also have the flexibility of creating Custom Application Signatures. This is very beneficial for Organizations that would want to tailor the Palo Alto 3220’s application-layer controls to suit their peculiar use cases.
(10) Logging and Reporting
This is another area where the Palo Alto 3220 really shines. The Logs and Reports provide you with detailed insights into your entire network infrastructure activity. This gives you comprehensive data for compliance purposes, forensic analysis, network health, and post-event analysis and learning.
(11) Scalability
As the digital world advances, so does the complexity of threats. Enterprise Network Infrastructures today, are designed with growth in view. The Palo Alto 3220 Firewall is designed with adaptability, continuous security updates, firmware updates, threat intelligence feeds, and patches that enable the machine tough and tenacious against the ever-dynamic threat landscape. With this, Organizations can build on their Cybersecurity infrastructure without disrupting their existing operations.
Final Thoughts
Using a Palo Alto Networks Firewall and in this case, the Palo Alto 3220, is a strategic decision you will be making to fortify your network security and address the ever-changing threat landscape. This Firewall is a very sophisticated machine that caters to the demands of mid-sized to large enterprises. As a Next Generation Firewall, the Palo Alto PA-3220 is a watchdog that delivers high-performance capabilities, advanced threat prevention mechanisms, and the kind of defense you need against the dynamic tide of cyber threats.
Get the Palo Alto PA-3220 on the Newegg Official Website (Free Shipping from the U.S.)
Get the Palo Alto PA-3220 on the Alibaba Official Website (Cashback Reward Available)
You may want to see the Fortinet FortiGate 100F and Cisco Firepower 1140



